[ad_1]
Cybercriminals prefer the Sliver framework over other popular solutions
The multifunctional C2 tool is increasingly being used for malicious purposes.
Management and control framework (C2) called Sliver is gaining more and more popularity among attackers. It is being promoted as an Open Source alternative to other C2 solutions like Cobalt Strike and Metasploit.
Sliver was developed BishopFox, a cybersecurity company. It is a cross-platform environment post-exploitation based golangintended for use by security professionals.
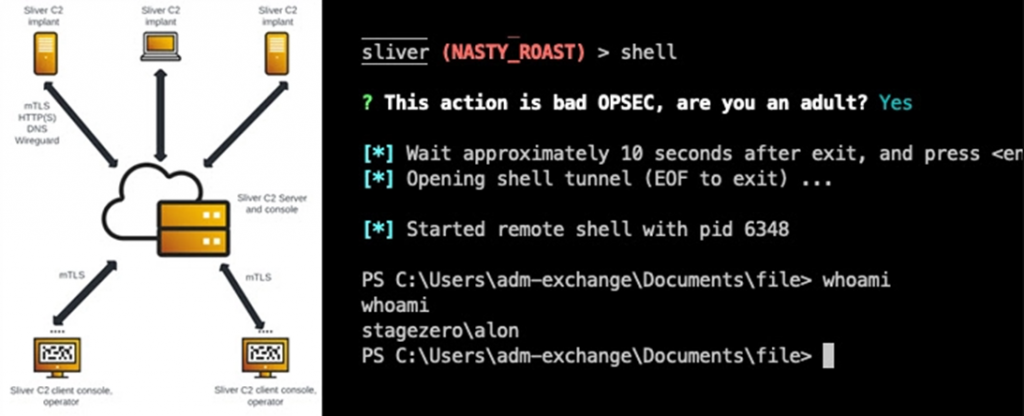
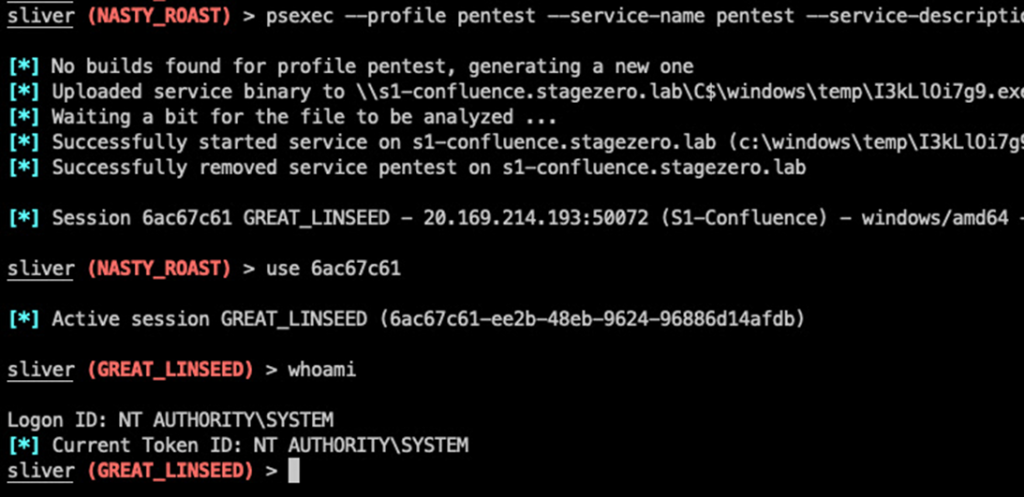
Sliver’s myriad malicious behavior modeling features, such as dynamic code generation, in-memory payload execution, and process injection, have made it an attractive tool for attackers seeking elevated access to a target system.
In other words, the software is used as a second stage to carry out the next steps in the attack chain. Already after the computer was compromised by means available to cybercriminals.
The hypothetical attack sequence detailed by Cybereason shows that Sliver can be used to elevate privileges on a system, followed by the theft of sensitive data.
In recent years, Sliver has been used in their attacks by the APT29 (aka Cozy Bear), Shathak (aka TA551) and Exotic Lily (aka Projector Libra) groups.
However, Sliver is far from the only C2 framework open source that can be used for malicious purposes. Last month, Qualys revealed how several hacker groups, including Turla, Vice Society, and Wizard Spider, were using the Empire framework to post-exploit and expand their positions. “Empire is an impressive post-exploitation platform with a wide range of capabilities,” said Akshat Pradhan, security researcher at Qualys.
[ad_2]
Source link
www.securitylab.ru