[ad_1]
Emotet malware uses social engineering to spread
Naive users themselves “open all doors” to the updated malware.
Emotet malware developers continue to improve their malware distribution tactics. Went on the move again social engineering.
The Emotet Trojan was first discovered in 2014. Clients of German and Austrian banks were attacked by the virus. Attackers used it to gain access to user credentials. Over time, the Trojan spread throughout the world.
Emotet later evolved into a dropper that installed other malware on devices. These programs caused real harm to the system.
In 2021, the Trojan was defeated after a coordinated shutdown of its infrastructure by the authorities, but by the end of the year it returned again. The virus spread mainly through phishing emails.
The development of Emotet is attributed to the TA542 cybercriminal group (aka Gold Crestwood or Mummy Spider). Emotet is currently distributed under the Malware as a Service model (MaaS). It is modular and can deploy multiple components to remote machines to extract sensitive information and perform other malicious activities.
Two recent additions to Emotet’s arsenal of modules include an “SMB spreader” designed to self-propagate the Trojan over a network, and a bank card data thief that runs in the Google Chrome browser. Researchers have long noticed constant attempts to retool Emotet to spread other malware, such as Bumblebee and IcedID.
AT recent Blackberry report the mechanism of distribution and operation of fresh Emotet is described in detail. Of greatest interest is how the malware generally gets on the victim’s computer. This happens with the help of the same phishing emails containing malicious .XLS files. But because Microsoft is constantly strengthening Office security, unrecognized .XLS documents from the web now automatically open in Protected View. This is bad news for Emotet, because the recorded scripts are, in fact, blocked at the application level. But the organizers of the malicious campaign figured out how to get around this limitation. They wrote detailed instructions for naive users to open “all tracks” to the virus.
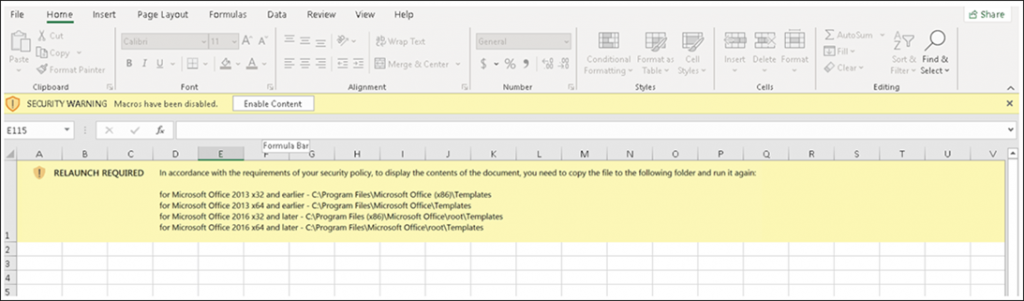
Fake security warning in uploaded .XLS file
As you can see in the image above, in the first line of a malicious document, cunning attackers placed an inscription on a familiar yellow background: “In accordance with the requirements of the security policy, to display the contents of the document, copy this file to the following location and run it again.”
If the user did not consider this message suspicious and performed the indicated actions, he, in fact, untied the hands of the virus. Next, Emotet will launch its malicious scripts and begin to spread over the local network. This is because any file executed from the “Office/Templates” location is ignored by Protected View, allowing embedded macros to run freely without any confirmation.
“Continuously evolving over the past eight plus years, Emotet continues to become more sophisticated in terms of evasive tactics. Additional modules are added to it for further distribution, new phishing campaigns are used. While the Emote may have been dormant for months, it has now returned with a vengeance, making it a threat to be reckoned with by both corporate and consumer users,” Blackberry said in the report.
[ad_2]
Source link
www.securitylab.ru