[ad_1]
Experts have found similarities between the Staff of Moses and the Ax of Abraham, which the Middle East uses against its enemies
Government hackers are waging a cyber war against their country’s adversaries.
Secureworks (Counter Threat Unit, CTU) team at in my new report links the activities of the politically motivated hacktivist group Moses Staff to a new threat actor called Abraham’s Ax that emerged in November 2022.
The connection between the factions is based on “several similarities in iconography, videography, and leak sites, suggesting they are run by the same group.
Gang logos
While Moses Staff (released in September 2021) is aimed at Israeli organizations , Abraham’s Ax is used in tandem to attack government ministries in Saudi Arabia. Experts suggested that this is a response to the leading role of Saudi Arabia in improving relations between Israel and the Arab countries.
For their part, the Abraham’s Ax hackers claim to be operating on behalf of Hezbollah (Arabic for “Party of Allah”), a Lebanese Shiite paramilitary organization and political party sponsored by Iran and Syria.
The Abraham’s Ax cybercriminals are likely using the same malware, which acts as a cryptographic cleaner to encrypt data without offering data recovery tools.
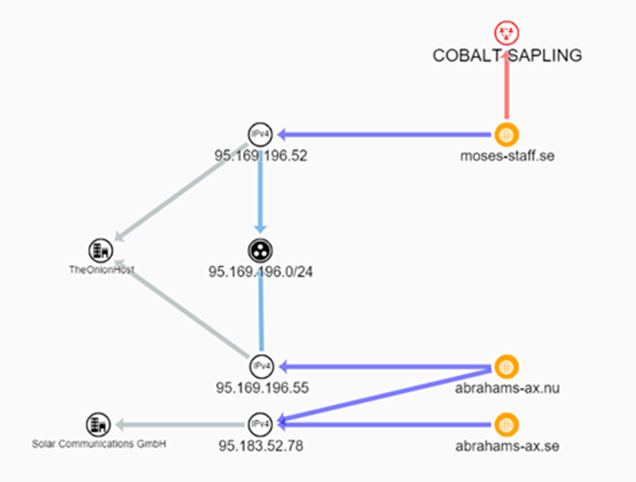
What’s more, both groups claim they are operating without financial incentive and their incursions are becoming more destructive. The connection between the two groups is also evidenced by the fact that WordPress-based leak sites were hosted on the same subnet in the early stages.
Communication between Moses Staff and Abraham’s Ax infrastructures
According to Secureworks researchers, Iran has a history of using proxy groups and fabricated identities to attack regional and international adversaries. Over the past couple of years, many new cybercriminal and hacktivist groups have emerged targeting Iran’s perceived enemies, who plausibly deny the government’s involvement in the attacks. And this trend, according to experts, will continue.
[ad_2]
Source link
www.securitylab.ru