Microsoft urges customers to secure Exchange on their own
Specialists from Redmond recommend carefully monitoring the version of the mail server software.
Microsoft encourages customers to keep their servers up to date Exchangeand take steps to harden the environment, such as enabling Windows Extended Security and configuring serialization payload certificate signing PowerShell.
“Attackers who want to use unsecured Exchange servers aren’t going anywhere. There are too many unpatched security aspects of on-premises Exchange environments that are valuable to those who want to steal data or perform other malicious activities. the message says Microsoft Exchange commands.
The corporation also emphasized that the proposed mitigation measures are only a temporary solution and that they may “may not be sufficient to protect against all attack variants.” Of course, to avoid most threats, users need to keep all Exchange security updates up to date.
Attacks on Exchange are very accessible due to a number of security flaws in the software. In the past two years alone, several vulnerabilities have been discovered in Exchange Server, including ProxyLogon, ProxyOracle, ProxyShell, ProxyToken, ProxyNotShell, and the ProxyNotShell workaround known as OWASSRF. Some of these vulnerabilities are widely exploited in the wild (ITW).
Antivirus company Bitdefender in his technical review published on January 24, called Exchange a “perfect target” for attacks, and also talked about some real-life attacks using ProxyNotShell / OWASSRF exploit chains since the end of November 2022.
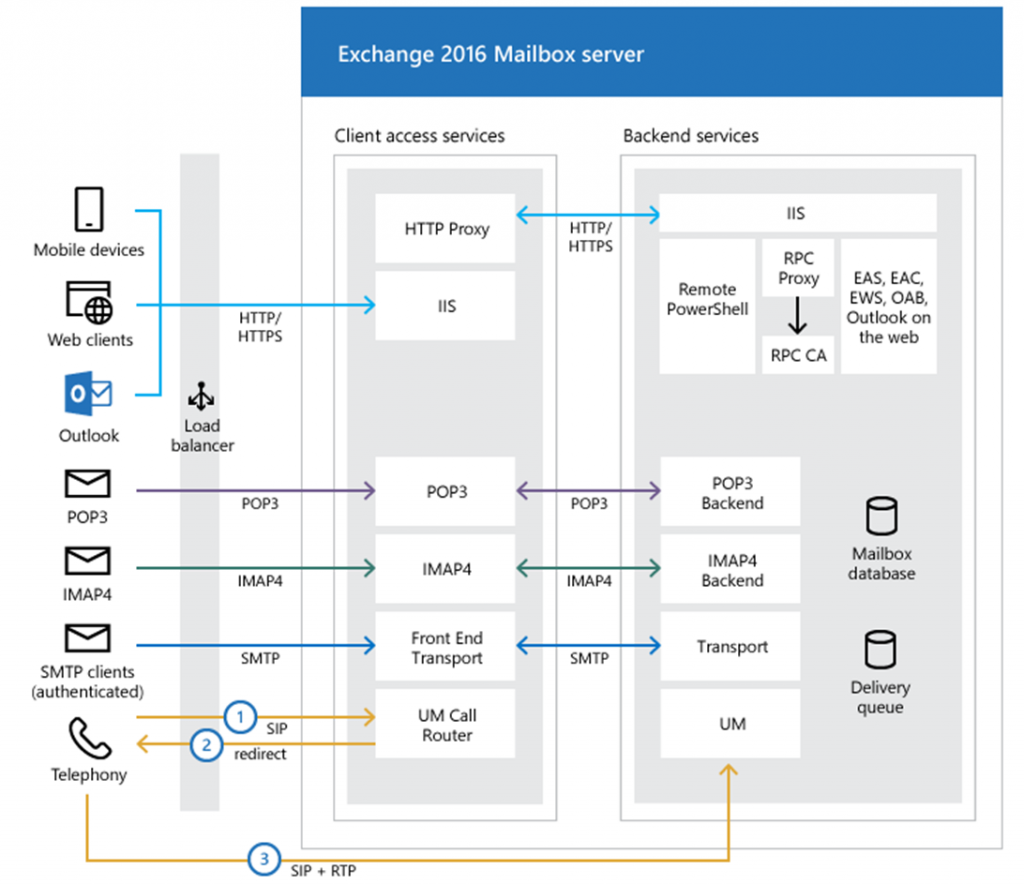
Exchange Client Access Protocol Architecture
“Exchange has a complex network of front-end and back-end services with legacy code to ensure backwards compatibility,” said Martin Zugek of Bitdefender.
It is also worth noting that some internal services run on behalf of the Exchange Server itself, which has system privileges. Exploits can provide an attacker with unauthorized access to a remote PowerShell service, effectively paving the way for the execution of malicious commands.
The attacks exploiting the flaws in ProxyNotShell and OWASSRF targeted arts, entertainment, consulting, legal, manufacturing, real estate and wholesale businesses located in Austria, Kuwait, Poland, Turkey and the United States, according to Bitdefender.
“These types of server-side request forgery (SSRF) attacks allow an attacker to send a processed request from a vulnerable server to others. This opens up access to resources or information that is otherwise not directly available,” says Bitdefender.
Most attacks are believed to be opportunistic rather than targeted. It culminates in attempts to deploy web shells as well as remote monitoring and management (RMM) software such as ConnectWise Control and GoTo Resolve.
Web shells not only offer a mechanism for permanent remote access, but also allow criminal organizations to carry out a wide range of follow-up activities and even sell access to other groups of hackers for profit.
In some cases, the staging servers used to host the payloads have already been compromised by the Microsoft Exchange servers themselves, suggesting that the same technique could have been used to scale up attacks.
There have also been unsuccessful attempts by attackers to download Cobalt Strike, as well as a Go-based implant codenamed GoBackClient, which comes with system information gathering and reverse shell capabilities.
Abuse of Microsoft Exchange vulnerabilities has also been a recurring tactic used by UNC2596 (aka Tropical Scorpius), Cuba ransomware operators (aka COLDDRAW). One attack used a sequence of ProxyNotShell exploits to remove the BUGHATCH loader.
“Although the initial vector of infection continues to evolve, and attackers quickly exploit any new opportunity, their actions after exploitation are predictable. The best defense against today’s cyberattacks is a defense-in-depth architecture,” said Zugek.
Source link
www.securitylab.ru