[ad_1]
Prilex returns: old malware gains new momentum
Compromised payment terminals can transmit bank card details to attackers.
Payment terminals supporting contactless payment use NFC-chips. The same chips are built into bank cards and mobile devices that support this technology. They allow you to make payments without inserting a card into the terminal. Contactless payments are very convenient and have skyrocketed in popularity since the COVID-19 pandemic.
The use of NFC chips also made it more difficult for attackers to steal bank card information with special malware. One of the popular malware for attacking payment terminals is Prilex. The malware was noticed for the first time back in 2014 and at first attacked only ATMs, and in 2016 it moved to PoS devices (Point-of-Sale), that is, payment terminals. In September we mentioned that researchers have started noticing Prilex attacks again after a long hiatus.
January 31 Kaspersky Lab informed about the appearance of at least three new variants of Prilex with version numbers 06.03.8070, 06.03.8072 and 06.03.8080. They were first released in November 2022.
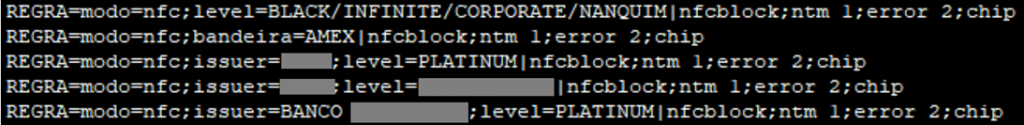
New versions of the malware independently detect whether NFC is being used for payments and automatically reject all contactless payments. A standard warning appears on the terminal that contactless payment cannot be made and you need to insert a card. This forces the victim to complete the transaction in the traditional way, which greatly simplifies the collection of card information through the payment terminal.
File with filtering rules blocking contactless transactions
Each NFC transaction generates a unique identifier that is valid for only one transaction. Therefore, even if such data is stolen, it will not give anything to scammers. However, Prilex uses a method of cryptogram manipulation and “ghost transaction” attacks, which allows attackers to make any transactions from a compromised card.
Also, in the latest versions of malicious software, a new feature has appeared – the ability to filter unwanted cards. For example, the condition must be met: map: credit, not debit; transaction limit: elevated etc. That is, the data of cards that do not meet the conditions will not be transferred to intruders. So they will not “run into” the limits and will be able to immediately “hit the jackpot”.
To protect yourself from this and other manipulations of scammers, you should follow the standard security measures:
- Refuse to pay at terminals with visible signs of hacking or non-working contactless payment. In such a place it is better to pay for the purchase in cash.
- Always check the amount of final transactions with those indicated on the terminal display. And in case of discrepancy between the amounts or the appearance of unnecessary transactions, immediately report this to the bank support.
- Refuse to use public Wi-Fi when logging into banking applications. Either mobile internet or VPNif there is no other option.
- Do not enter your PIN in front of others. Do not share your CVV code or SMS codes with anyone.
And remember, don’t panic even if the money has been stolen. The law is on your side: any card transaction can be challenged if there is enough evidence that you have become a victim of fraud.
[ad_2]
Source link
www.securitylab.ru