[ad_1]
PlugX worm now silently spreads through USB drives
By replacing and hiding files, the new PlugX variant will now quickly spread to many systems.
Palo Alto Networks Unit 42 Cybersecurity Researchers discovered a new sample of PlugX that silently infects attached removable USB drives to spread malware to additional systems.”
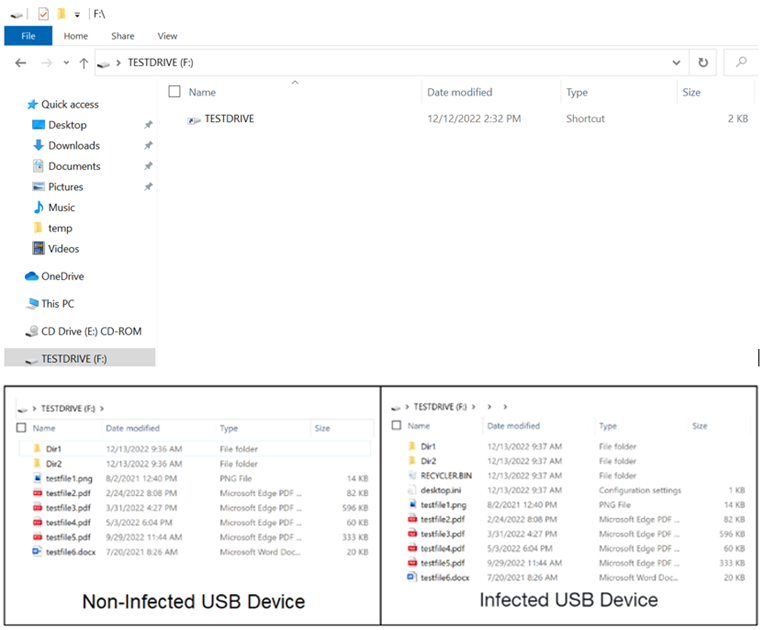
Worm PlugX infects USB devices by hiding its activity from the Windows file system, i.e. the user will not know that his USB device is infected or is already being used to steal data from the target network.
The USB variant of PlugX uses the special Unicode character U+00A0 (non-breaking space ” “) to hide files on a connected USB device. The space hides the name of the malicious directory rather than leaving an unnamed folder in Explorer.
Ultimately, the LNK shortcut created in the root folder of the USB drive is used to launch malware from a hidden directory. The PlugX sample not only injects malware into the host, but also copies it to any connected USB device, disguising it inside the trash folder.
The shortcut file has the same name as the USB device and has a local drive icon, and existing files in the root of the removable device are moved to a hidden folder created inside the “shortcut” folder.
Every time the user clicks on a shortcut to a file from an infected USB, PlugX launches Windows Explorer and passes the directory path as a parameter. Files on the USB device are then exposed from hidden directories and PlugX malware infects the host.
This attack method is based on the fact that Windows Explorer does not show hidden items by default. The attack is notable for the fact that malicious files in the “recycle bin” are not displayed if this setting is enabled. This means they can only be seen on a Unix-like OS like Ubuntu, or by mounting a USB device in a forensics tool.
New files written to the root folder of the USB device after infection are moved to a hidden folder. Because the Windows shortcut file mimics a USB device file and the malware displays the victim files, the user unwittingly continues to distribute PlugX malware.
Unit 42 also detected a second PlugX variant that, in addition to infecting USB devices, additionally copies all Adobe PDF and Microsoft Word files from the host to another hidden folder on the USB device created by the malware.
With the latest development, PlugX joins other malware families such as ANDROMEDA and Raspberry Robin , which added the ability to spread through infected USB drives. This means that PlugX development is still thriving, at least among some technically skilled attackers, and remains an active threat.
[ad_2]
Source link
www.securitylab.ru