Sneaky Buffer: Tor Trojan Browsers Massively Steal Russian Cryptocurrency
A simple but effective trick brought the scammers about 400 thousand dollars in profit.
Analysts of Kaspersky Lab fixed a surge of trojanized installers Tor Browser aimed at Russians and residents of Eastern Europe. Using clipboard hijacking malware, attackers can intercept users’ cryptocurrency transactions on infected computers.
The researchers warn that while this attack is not new or particularly ingenious, it is still very effective and widespread. With its help, hackers successfully infect many users around the world.
Experts attribute the spread of Tor Browser Trojan installers in Russia to the official ban on the Tor Project website by regulatory authorities. At the end of 2021, Roskomnadzor blacklisted the site, it cannot be opened on the territory of the Russian Federation without using VPN. Therefore, users who are worried about their security or want to bypass regional restrictions often download the browser from unofficial sites, some of which contain malicious software.
Tor Browser is a specialized web browser that allows users to surf the web anonymously by hiding their IP address and encrypting outgoing traffic. Tor is also often used to access special “onion” domains that are not indexed by standard search engines and are not accessible through regular browsers.
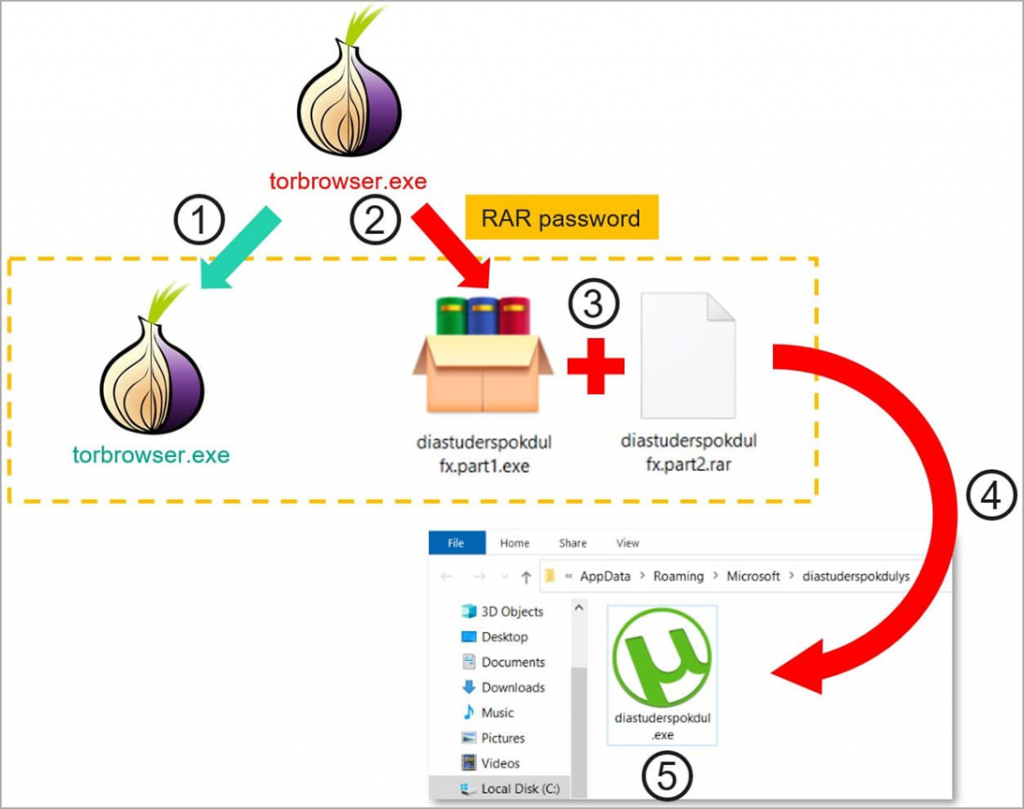
Kaspersky Lab researchers report that distributed Trojan installers usually contain a standard version of the Tor browser, which is often outdated, as well as an executable file hidden in a password-protected “.rar” archive configured to self-extract on the user’s system.
While the standard Tor browser runs in the foreground, the aforementioned password-protected archive extracts malware in the background, launches it, and adds it to Windows startup. In addition, the malware uses the uTorrent icon to hide in a compromised system without arousing suspicion.
Scheme of infection through a trojanized Tor Browser
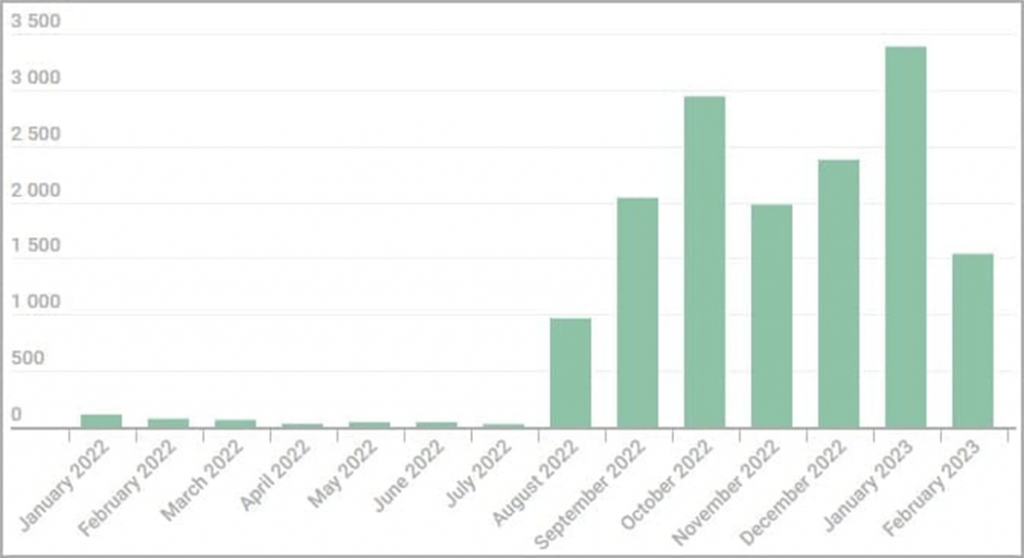
Kaspersky researchers discovered a total of about 16,000 Tor installers between August 2022 and February 2023. While the malware campaign is primarily aimed at users in Russia and Eastern Europe, Trojan browsers have also been seen in the United States, Germany, China, France, the Netherlands, and the United Kingdom.
Trojan versions of Tor Browser discovered in the last year
The malware itself works quite simply, but it is no less interesting for that. Because cryptocurrency wallet addresses are long and difficult to type, users typically copy them to the clipboard and then paste them into a specific program or website.
The malware in the described campaign is precisely what it monitors in the clipboard for data similar to the addresses of cryptocurrency wallets, and then replaces it with an address belonging to the attackers. Thus, when the user makes a transaction, he himself will indicate the attacker’s wallet in the transfer field and personally “give” him his cryptocurrency.
The researchers recorded the use of over a thousand different cryptocurrency addresses in each malware sample. From a list hard-coded by attackers, one specific address is randomly selected, to which the victim’s cryptotransaction then goes.
This approach makes it very difficult to track the movement of the cryptocurrency in the blockchain, as well as blocking the attacker’s wallets. According to the company, almost $400,000 worth of bitcoin was stolen during the entire duration of the malicious campaign.
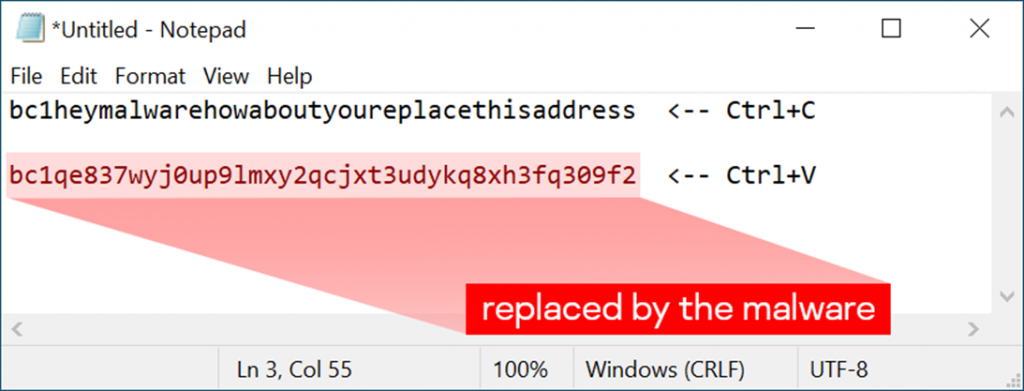
According to Kaspersky Lab experts, it is quite easy to check your computer for such malicious software. Simply copy the following crypto wallet address to the clipboard: “bc1heymalwarehowaboutyoureplacethisaddress”, and then paste it, for example, into a regular notepad. If the address has changed, then there is a “cossack” in the system that replaces the data copied to the buffer.
Simple check for malware in the system
To protect yourself from clipboard thieves, you should only install software from official sources, in this case from the Tor Project website, but using a VPN. And when making crypto transactions, it is worth double-checking the wallet to which the currency will go, before confirming the operation.
Source link
www.securitylab.ru