[ad_1]
White hat hackers to release VMware vRealize Log RCE exploit soon
The sensational grouping Horizon3 once again demonstrates why it is important to install security updates on time.
Security researchers from the team Horizon3 will be posted online next week exploittargeting a chain of vulnerabilities to enable remote code execution on devices with VMware vRealize Log Insight.
Now known as VMware Aria Operations for Logs, the program makes it much easier for VMware administrators to analyze and manage system logs.
On January 24, VMware fixed four security vulnerabilities in this log analyzer, two of which are critical and allow an unauthorized party to remotely execute code. Both vulnerabilities are marked as critical with baseline ratings CVSS 9.8/10. They can be used by attackers in low complexity attacks that do not require authentication.
One of them (CVE-2022-31706) is a directory traversal vulnerability that can be used to inject files into the operating system. And the second one (CVE-2022-31704) is an access control vulnerability.
VMware also fixed a deserialization vulnerability (CVE-2022-31710) that could cause a system crash, as well as an information disclosure vulnerability (CVE-2022-31711) that could be used to access sensitive data.
Horizon 3 Twitter announcement
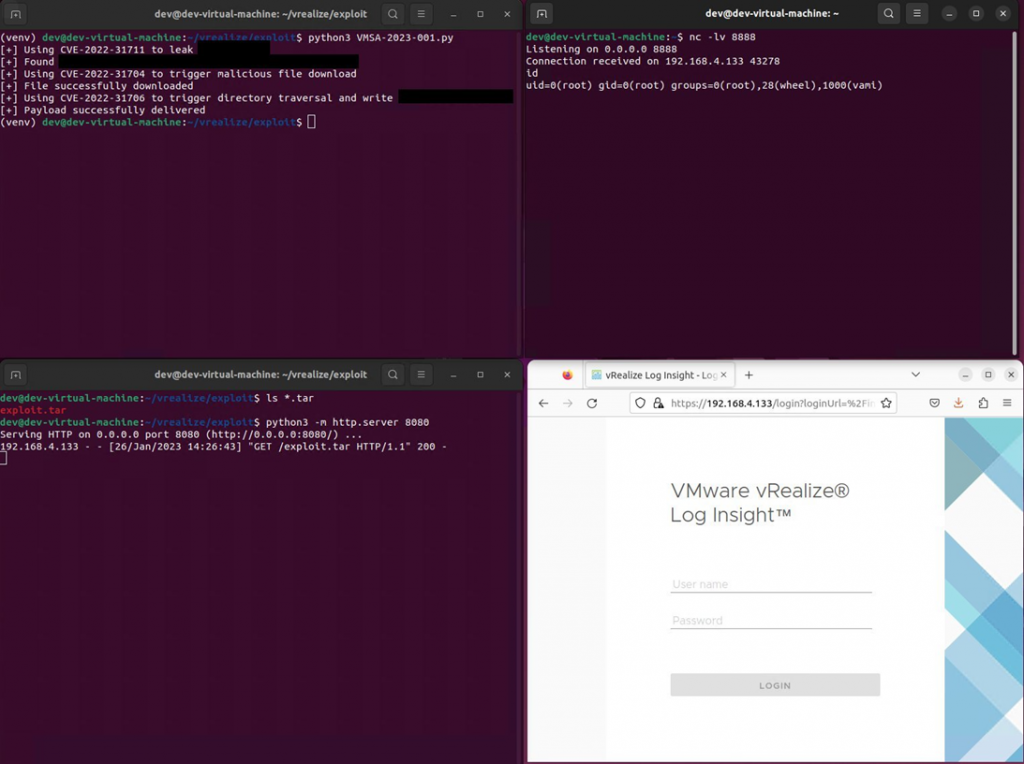
On January 26, the Horizon3 team alerted VMware administrators that they have managed to create an exploit that combines three of the four vulnerabilities already patched by VMware to remotely execute code as root.
All vulnerabilities can be exploited in the default VMware vRealize Log Insight appliance configuration. The exploit can be used to gain initial access to corporate networks (through devices connected to the Internet) and to navigate the network with stored credentials.
A day later, Horizon3 published a blog post with more information, including a list of Indicators of Compromise (IoC) professionals can use to detect signs of usage on their networks.
With the aforementioned exploit, attackers can obtain sensitive information from logs on Log Insight hosts, including API keys and session tokens, which can help break into additional systems and compromise the environment even further.
VMware vRealize Log Insight unauth RCE exploit
James Horsman, researcher at Horizon3, said there are only 45 vulnerable devices on the Internet right now. It’s relatively small. This number is to be expected, as VMware vRealize Log Insight is designed for internal access to organization-specific networks. Connecting from outside is usually not possible. However, it is not uncommon for cybercriminals to exploit vulnerabilities in already compromised networks to expand the aforementioned access.
In May 2022, Horizon3 released an exploit for CVE-2022-22972, a critical authentication bypass vulnerability affecting several VMware products and allowing hackers to gain administrator rights.
[ad_2]
Source link
www.securitylab.ru