[ad_1]
The magic cart carries the French by the nose, replacing the forms of payment in online stores
During the Magecart campaign, hackers spoof checkout pages and steal card details.
Company specialists Malwarebytes report that in an ongoing campaign by Magecart, attackers are using fake checkout pages to harvest sensitive user data.
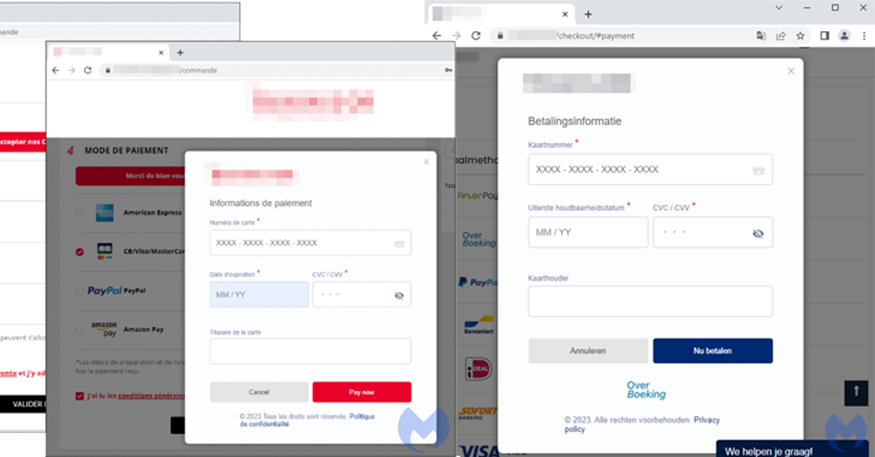
The cybercriminals used the real logos of the compromised store and set up a modal window to completely hack the checkout page. It is noteworthy that skimmer looks more authentic than the original payment page.
The term Magecart is generic and refers to several groups of cybercriminals who use onlineskimming to steal personal data from websites – most often, customer details and payment information on e-commerce sites.
A discovered campaign targeting an unnamed French online travel accessories store powered by PrestaShop CMS used a skimmer called “Kritec” to intercept the checkout process and display a fake payment dialog for victims. Kritec posed as Google Tag Manager to avoid suspicion and detection.
The skimmer code is heavily obfuscated, and the malicious mode is only loaded when the victim selects a payment card as a payment method on the compromised site. Once the card details are collected, the victim is briefly shown a fake payment cancellation message, and then the user is redirected to a real payment page, after which the payment is successfully completed.
Fake (left) and legitimate (right) forms of payment
In addition, the skimmer delivers cookie-file to mark the current session as ended. If the user comes back and tries to make the payment again, the malicious modal will no longer be displayed.
The threat actors behind this operation are said to be using different domains to host the skimmer, which are given similar names: “[имя магазина]-loader.js”. This suggests that modal windows are configured individually for each attacked online store.
[ad_2]
Source link
www.securitylab.ru