[ad_1]
Unknown hackers have resurfaced after a long hiatus and are spying in North Africa
Stealth Soldier’s hidden backdoor and multi-stage infection chain gives hackers access to sensitive data of victims.
Specialists check point Research has uncovered a series of highly targeted spy attacks in North Africa and linked it to a previously unknown “Stealth Soldier” modular backdoor.
According to security researchers report , a campaign aimed primarily at the people of Libya, focused on espionage and tracking. The Stealth Soldier backdoor includes the following features:
- file exfiltration;
- screen and microphone recording;
- registration of keystrokes (keylogging);
- stealing information from the browser.
The Check Point Research team highlighted that the Stealth Soldier infrastructure bears similarities to the infrastructure used in the previous campaign, known as Eye on the Nile. Operation Eye on the Nile targeted Egyptian civil society in 2019, but similarities to Stealth Soldier suggest a possible resurgence of the attacker after a long hiatus.
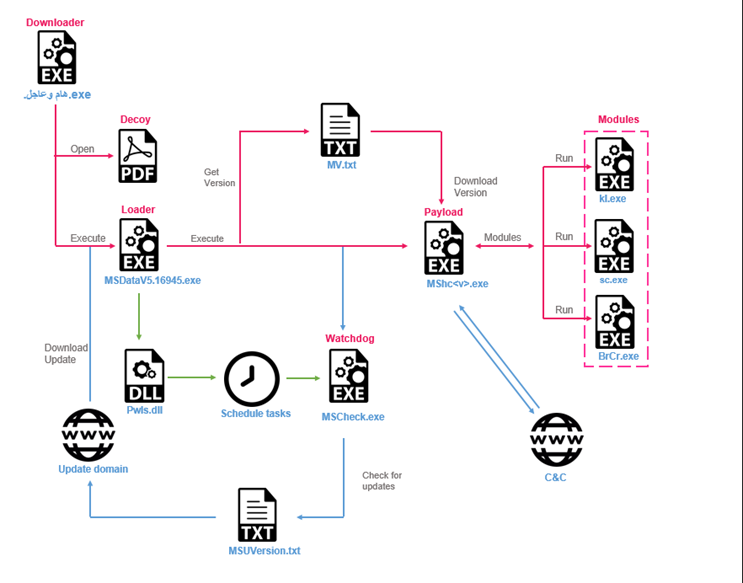
Stealth Soldier Infection Chain
The flow of execution for all versions of Stealth Soldier begins with the launch of the bootloader, which executes the infection chain. While the mechanism for delivering the bootloader is currently unknown, experts speculate that the bootloader was delivered through social engineering. In total, during the infection process, the malware downloads 6 files from C2 servers. The main ones are:
- Loader – Loads PowerPlus, an internal module for executing PowerShell commands, and uses it to create persistence for the watchdog. Launches the latest Stealth Soldier payload;
- Watchdog – periodically checks for an updated version of the bootloader and launches it. Constant use of a scheduled task and a registry start key;
- Payload – collects data, receives commands from the C&C server and executes modules.
Experts discovered various versions of the backdoor, the latest of which was delivered to the target device in February 2023. The oldest version found was compiled in October 2022.
It is worth noting that Stealth Soldier’s C2 servers are connected to a larger set of domains, some of which masquerade as sites belonging to the Libyan Foreign Ministry, which indicates the use of phishing campaigns for surveillance and espionage operations against Libyan and Egyptian targets.
The security researchers added that the results of the analysis highlight the importance of strong cybersecurity measures to counter targeted spyware attacks, especially in regions where such threats are widespread. The experts concluded that, given the modularity of the malware and the use of multiple stages of infection, it is likely that cybercriminals will continue to develop their tactics and deploy new versions of Stealth Soldier in the near future.
[ad_2]
Source link
www.securitylab.ru