[ad_1]
Alarming spike in TrueBot activity revealed thanks to new delivery vectors
From downloading a file from Google Chrome to stealing data from a host.
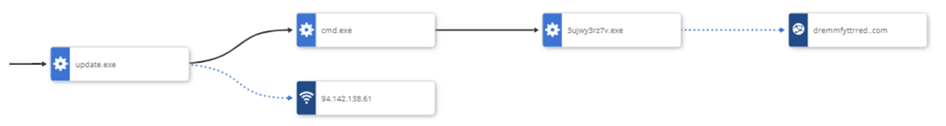
Cybersecurity researchers VMware reported that in May 2023 there was a spike in downloader activity truebot. The chain of attacks begins with the download of the executable file ” update.exe ” from Google Chrome, suggesting that users are being lured into downloading malware under the guise of a software update.
Once launched, “update.exe” establishes a connection to a well-known TrueBot IP address located in Russia to obtain the second stage executable file (“3ujwy2rz7v.exe”), which is subsequently run using the command line Windows. The downloaded executable connects to the C2 server and retrieves sensitive information from the host. The file also has the function of listing processes and systems.
TrueBot infection chain
The main function of TrueBot is to collect information from the host and deploy next stage payloads such as Cobalt Striketrojan Flawed Grace and a previously unknown utility for data exfiltration Teleport. Next, lateral movement and data collection is performed, and then the binary file of the Clop ransomware is launched. An analysis of the Teleport utility showed that the software is used exclusively to collect files from OneDrive and Downloads, as well as messages from Outlook.
VMware experts concluded that TrueBot can be a particularly dangerous infection for any network. Once inside a system, TrueBot can quickly escalate into larger malware, much like ransomware spreads over a network.
TrueBot is a Windows malware downloader attributed to the Silence group (according to GroupIB), which is presumably related to Evil Corp. The assumptions about the connection of the groups are based on the fact that Evil Corp uses a worm Raspberry Robin to deploy droppers on compromised networks.
According to Cisco Talos, the delivery of the Raspberry Robin resulted in creating a botnet from over 1000 systems , which are distributed all over the world, in particular in Mexico, Brazil and Pakistan. Moreover, the TrueBot campaign botnetted over 500 Windows servers located in the US, Canada and Brazil.
Note that in 2019 the Silence hacker group organized a mass phishing campaign with more than 80 thousand recipients. Among them are employees of Russian financial institutions, most of which are banks and large payment systems. During the distribution, the TrueBot loader was delivered to the devices of the victims.
[ad_2]
Source link
www.securitylab.ru