[ad_1]
Attackers are distributing a new stealer under the guise of CapCut
Fraudsters take advantage of the fact that the application is banned in other countries and offer users alternative download methods.
Specialists from cybersecurity company Cyble discovered two campaigns during which attackers distribute malware under the guise of cap cut – popular video editor for TikTok.
CapCut is the official video editor from ByteDance for TikTok. The application has more than 500 million downloads on Google Play alone, and more than 30 million users visit the program website per month.
The popularity of the app, as well as its ban in Taiwan, India, and other countries, has forced users to look for alternative ways to download the program. Cybercriminals take advantage of these restrictions by creating fake sites that distribute malware that mimics CapCut installers.
It is not known how victims get to these sites, but attackers usually use black hat search engine optimization (Black Hat SEO)advertising in search and social networks to promote sites.
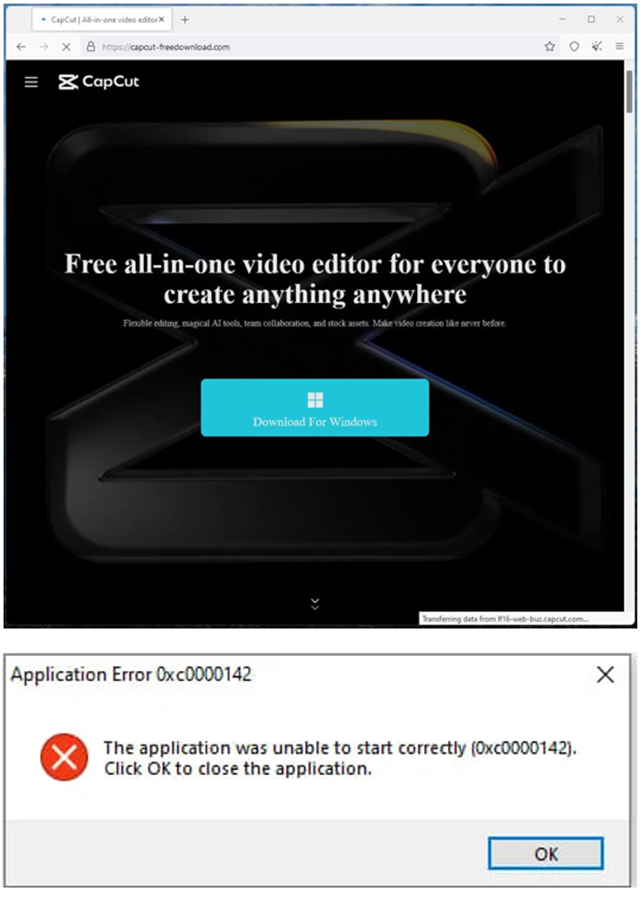
During the first campaign victim downloads a stealer from a fake site Offx Stealer, designed for Windows 8, 10, and 11. When the victim launches the downloaded file, they receive a fake error message stating that the application failed to launch. However, Offx Stealer continues to run in the background.
Fake site CapCut and displayed application error
The malware collects:
- passwords and cookie-files from web browsers and certain file types (.txt, .lua, .pdf, .png, .jpg, .jpeg, .py, .cpp and .db) from the user’s desktop folder;
- data from Discord and Telegram;
- data from cryptocurrency wallet applications (Exodus, Atomic, Ethereum, Coinomi, Bytecoin, Guarda and Zcash);
- information from the UltraViewer and AnyDesk remote access software.
All stolen data is stored in a randomly generated directory in the “%AppData%” folder, archived and then sent to hackers in a private Telegram-channel. After the files are exfiltrated, the created directory is deleted to erase the traces of the infection.
Second campaign delivers the “CapCut_Pro_Edit_Video.rar” archive to devices, which, when opened, launches the script PowerShell. The PowerShell script downloads the final Redline Stealer payload and the .NET executable. (needed to bypass the Windows AMSI security feature, allowing Redline Stealer to run undetected).
To avoid the risk of malware infection, download software directly from official sites, not from sites shared by other users on social networks or private messages. As a reminder, CapCut is available on “capcut.com”, Google Play (for Android) and App Store (for iOS).
[ad_2]
Source link
www.securitylab.ru