[ad_1]
Hackers were unable to share the computing power of Kubernetes
Cryptojacking operation ended with a confrontation between two hacker groups
Cybersecurity researchers CrowdStrike recently uncovered another illegal cryptocurrency mining campaign. The victim of the attackers this time was the platform Kubernetes. And the operation itself marks the first time that cybercriminals have abandoned cryptocurrencies. Monero, which is currently the most widely mined coin in cryptojacking campaigns. Instead, cybercriminals preferred the Dero crypto coin. This may be due to the fact that Dero is slightly more profitable to mine, and the coin also provides anonymization functions at least as good as Monero.
Kubernetes is one of the most popular container management systems developed by Google and is designed to automate the deployment, scaling and management of containerized applications. Kubernetes has a very impressive computing power, so it is not surprising that crypto scammers are interested in the company.
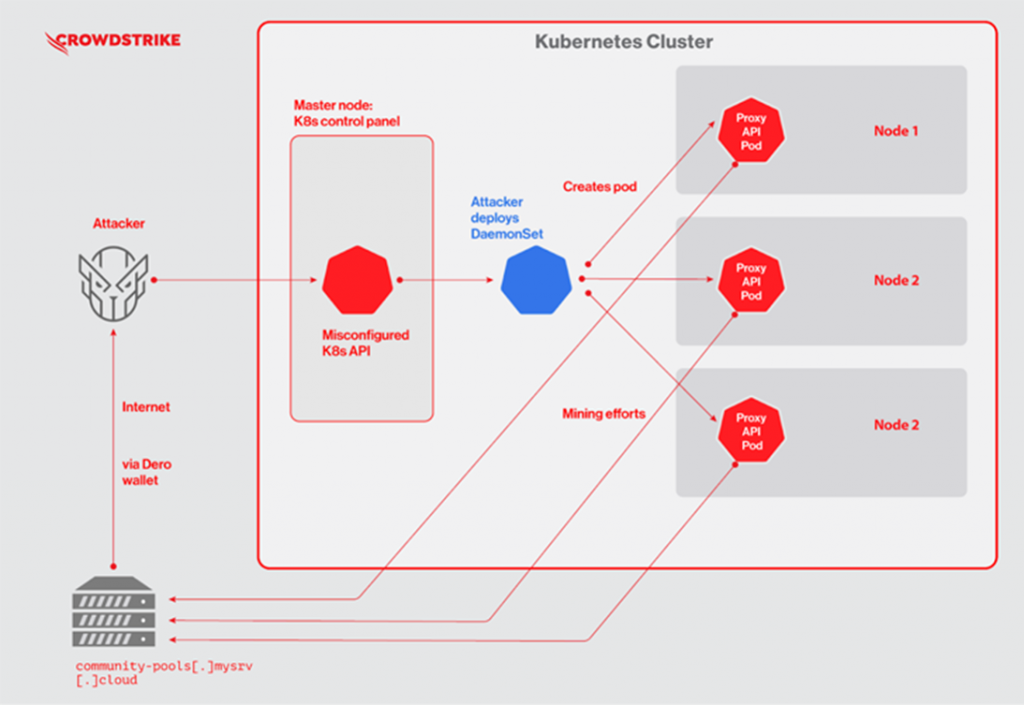
The attack, attributed to an unknown financially motivated group of hackers, began by looking for insecure Kubernetes clusters with the ability to anonymously authenticate and then injecting a payload into them. Then, a malicious mining module disguised as a legitimate system container was deployed on each such cluster, making malicious activity harder to detect.
Diagram of a recent attack on Kubernetes clusters
CrowdStrike also stated that it also detected other malicious activity in parallel, targeting public Kubernetes clusters. It is noteworthy that a completely different hacker group was already operating, which managed to detect the presence in API Kubernetes competitor, “drive” him and connect the mining of the Monero cryptocurrency to your wallet. More like a showdown between Mexican cartels than a confrontation between hackers.
What to do, everyone wants to grab their “piece of the pie” and fight for it as best they can. What happened once again proves the attractiveness of cryptojacking operations for modern hackers. Everyone loves money, and when all you need to get it is to connect to an open high-performance server, it’s apparently impossible for attackers to resist.
[ad_2]
Source link
www.securitylab.ru