[ad_1]
Malware exploited Realtek SDK critical bug in millions of attacks
Hackers are attacking IoT devices en masse.
Between August and October last year, specialists from Palo Alto Networks observed significant activity in exploiting the CVE-2021-35394 vulnerability, exploited by several hacker groups at once. It accounts for more than 40% of the total number of incidents. The threat has a severity rating of 9.8 out of 10.
In September 2022, a major new malware emerged to botnet called “RedGoBot” aimed at IoT devices (IoT) vulnerable to CVE-2021-35394.
Unit 42 researchers noticed that exploitation of the vulnerability continued throughout December. As a result of these attacks, three different payloads were delivered to the victims:
- a script that performs command-line operations on the target server to download malware;
- an embedded command that writes a binary payload to a file and executes it;
- an embedded command that restarts the server.
Most of these attacks originate from botnet malware families such as Mirai, Gafgyt, Mozi and their derivatives. In April 2022, the Fodcha botnet was seen exploiting CVE-2021-35394 to carry out DDoS attacks.
RedGoBot also exploited a DDoS vulnerability in September. The botnet can perform DDoS attacks over HTTP, ICMP, TCP, UDP, VSE, and OpenVPN protocols and supports various flooding methods.
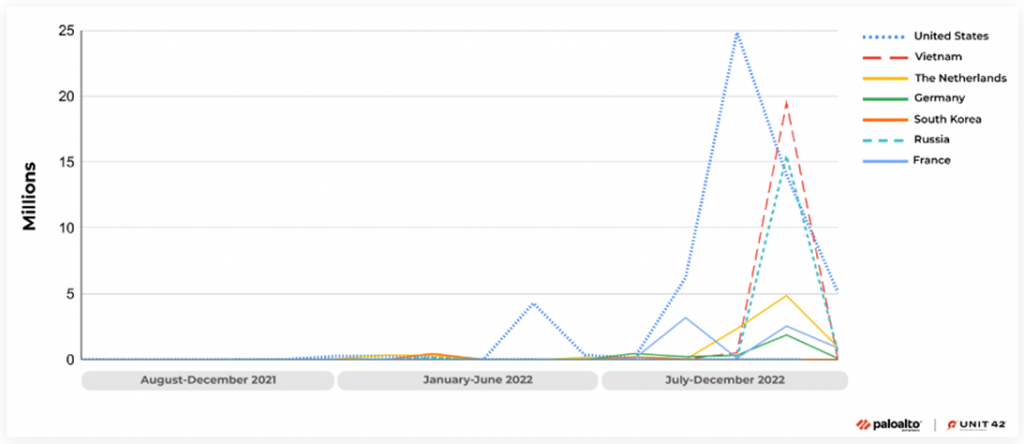
Specialists from Unit 42 recorded activity using CVE-2021-35394 from all over the world, but almost half of the attacks came from the United States. It is possible that the hackers used VPNs or proxy servers to hide the actual source of the attack.
Sources of attacks on CVE-2021-35394 by country
“From August 2021 to December 2022, we observed a total of 134 million hack attempts targeting CVE-2021-35394, with 97% of these attacks occurring after the start of August 2022. More than 30 countries were involved as the source of the attack, with the United States being the largest source of attacks at 48.3% of the total. Vietnam, Russia, the Netherlands, France, Luxembourg and Germany were also among the top seven countries from which, according to our observations, attackers took part in these attacks, ”the Unit 42 report says.
CVE-2021-35394 is a critical vulnerability in Realtek Jungle SDK version 2.x to 3.4.14B caused by multiple memory corruptions that allow remote unauthorized attackers to perform arbitrary command injection.
Realtek chipsets are ubiquitous in the IoT world, and even as the Taiwanese chipmaker releases security updates to quickly fix problems in its products, supply chain complexities delay their delivery to end users.
Realtek closed the vulnerability as early as August 15, 2021, however, often many users of IoT devices use them on a “set it and forget it” principle and do not update the software to the latest version in a timely manner.
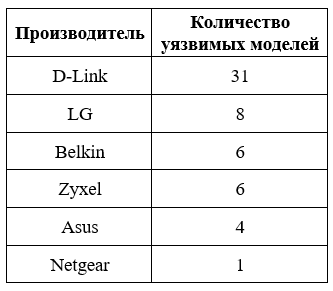
Devices vulnerable to CVE-2021-35394
The spike in exploitation of CVE-2021-35394 almost a year after Realtek released security patches indicates that hardware manufacturers and end users are at fault. It is possible that some affected devices are no longer supported by manufacturers, and they have not released an update for them at all. In some cases, an update with a fix may have been released, but users could not/won’t install it.
If your device has already been infected, it is recommended that you perform a factory reset, set a strong administrator password, and then apply any available firmware updates.
CVE-2021-35394 is still expected to be actively exploited in the first half of 2023 due to difficulties in the chain of delivery of fixes to devices.
[ad_2]
Source link
www.securitylab.ru