[ad_1]
Manifest Confusion Vulnerability in NPM Repository Allows Attackers to Inject Hidden Dependencies
“Do you see dependencies? And I don’t see it, but they are there.”
Popular repository for developers NPM suffers from a security issue called Manifest Confusion, which undermines trust in packages and allows attackers to hide malicious code in dependencies or execute malicious scripts when installing packages.
NPM is a package manager for a programming language JavaScriptthe default for a widely used environment Node.js. Today, over 17 million developers around the world use NPM, downloading about 208 billion packages per month.
Darcy Clark, former engineer GitHub, noticed on manifest confusion in his blog, explaining that while his former employer had been aware of the issue since at least November 2022, little had been done to address the risks associated with it.
The NPM registry is extremely popular among developers because it contains a wide range of packages that can be used to extend the functionality of an application without the need for additional development.
However, the repository’s popularity makes it a prime target for attackers who want to distribute malicious packages to take over developers’ computers and cut into the supply chain.
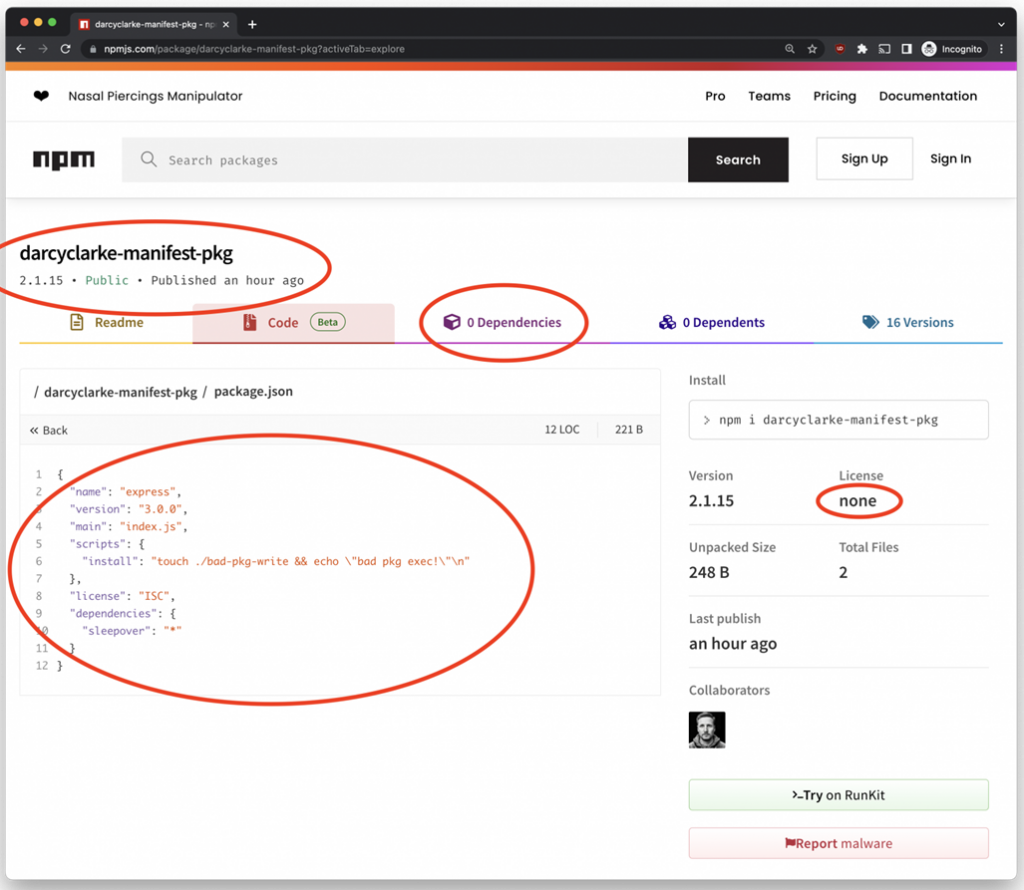
Manifest confusion occurs when there is a mismatch between the package information provided in the NPM registry and the actual “package.json” file in the published package archive used to install it.
Both the manifest information sent to NPM when the package is published and “package.json” contain information about the package name, version, and other metadata such as scripts used in deployment, build dependencies, and so on. But this data is sent to NPM separately, and the platform does not check their correspondence with each other. That is why the information may differ, but no one will know about it until they study the contents of such a package.
This allows attackers to modify the manifest data to remove dependencies and scripts listed on the package page in the repository. However, these scripts and dependencies still exist in the “package.json” file and will be executed when the package is installed.
The confusion in the manifests is shown in the image below, where you can clearly see that the package page doesn’t list any dependencies, but “package.json” does.
A visual demonstration of the Manifest Confusion vulnerability
Risks arising from such inconsistencies include cache poisoning, installation of unknown dependencies, malicious script execution, and downgrade attacks.
“It’s not just about hidden dependencies. Manifest confusion also allows attackers to include hidden installation scripts in the package that won’t show up on the NPM site and won’t be captured by most security tools.” warned Feross Abuhadijeh, CEO of the company Socket.
Darcy Clark’s report somehow caught the attention of NPM management. According to company representatives, they are working on the problem. Until then, authors and maintainers are encouraged to remove all dependencies on their package manifest data and obtain all metadata except name and version from “package.json” files.
Another defensive measure would be to use a registry proxy between the package database and the NPM client, which could implement a match check between the manifest data and the information in the archive.
[ad_2]
Source link
www.securitylab.ru