[ad_1]
The Trojan is not detected by antiviruses and extracts all information about the target.
Securonix Researchers discovered RAT-based Trojan Pythonwhich gives its operators full control over compromised systems.
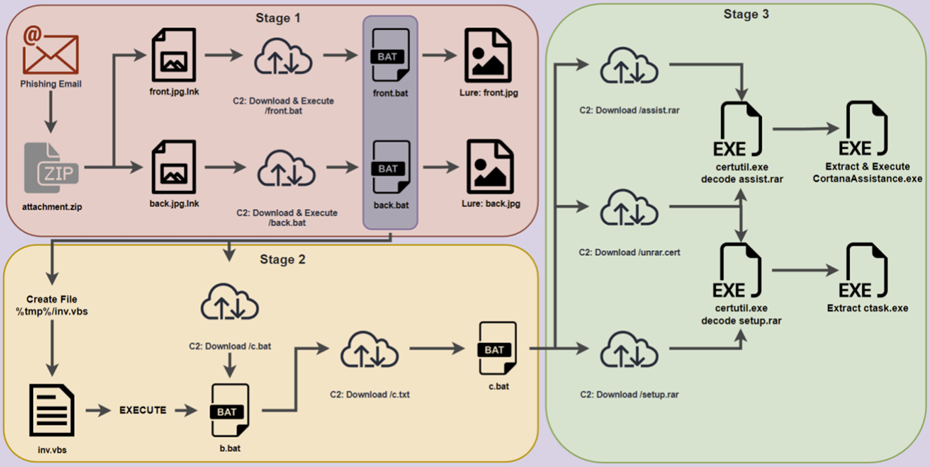
The experts named the Trojan PY#RATION. It uses the WebSocket protocol to communicate with the command and control server (C2) and to extract data from the victim host. The PY#RATION malware is distributed through a phishing campaign that uses password-protected ZIP archives containing two LNK tags disguised as images front.jpg.lnk and “back.jpg.lnk“.
When launching the shortcuts, the victim sees photos of the driver’s license. At this time, malicious code is executed to communicate with C2 and download two TXT files “front.txt” and “back.txt”, which are then renamed to BAT files to execute malware.
When launched, the malware creates the “Cortana” and “Cortana/Setup” directories in the user’s temporary directory and then downloads, unpacks, and runs additional executable files from that location. Persistence is established by adding the “CortanaAssist.bat” batch file to the user’s startup directory. The use of Cortana aims to disguise malware entries as system files.
PY#RATION is RAT– a Python-based Trojan packaged into an executable file using automatic packagers such as “pyinstaller” and “py2exe” that can convert Python code into Windows executables that include all the libraries needed to execute it.
This approach results in an increase in payload size, which helps malware avoid detection.
Among the features of the PY#RATION RAT version are the following:
- network enumeration;
- transferring files from a compromised system to C2 or vice versa;
- keylogging;
- execution of shell commands;
- enumeration of hosts;
- extracting passwords and cookie-files from browsers;
- theft of data from the clipboard;
- Detection of antivirus tools on the device.
The use of the WebSocket protocol allows the Trojan to communicate with C2 over a single TCP connection using ports that are usually left open (80 and 443). At the moment, details about specific campaigns using this malware and its targets, distribution volume, and the operators behind it remain unclear.
[ad_2]
Source link
www.securitylab.ru