[ad_1]
New RA Group breaks into cyberspace with its own ransomware
But there is one caveat – the program is based on the leaked source code of the Babuk ransomware.
A new group of hackers called “RA Group” is attacking pharmaceutical, insurance, financial and manufacturing companies in the US and South Korea with ransomware.
The group began operations in April 2023, when hackers launched a site on the dark web to publish stolen data from their victims. So, hackers use the tactic “double extortion”prevalent among other ransomware groups.
By data teams Cisco Talos, RA Group uses a ransomware based on leaked Babuk ransomware source code .
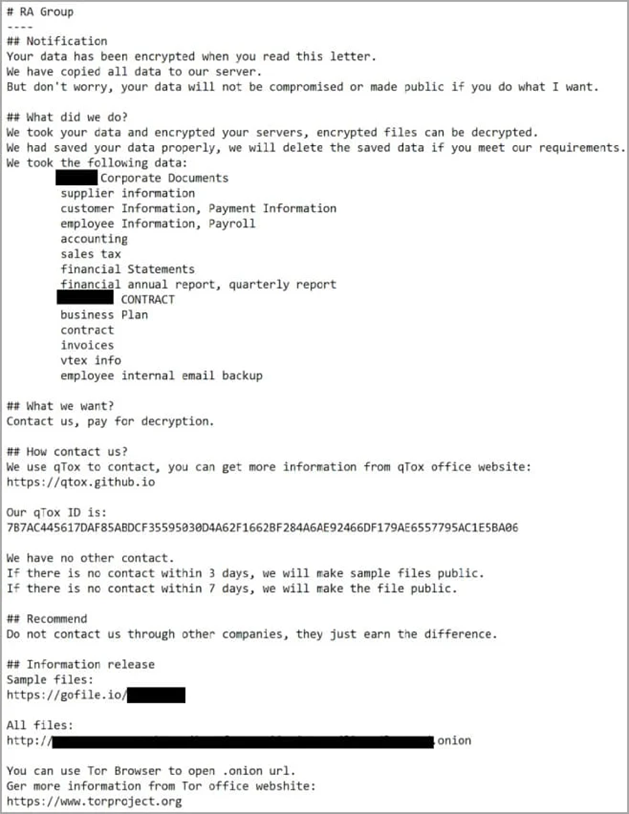
A feature of the RA Group is that in each attack, the victim will receive an individual ransom note written specifically for the target organization. In addition, the memo file gets a name that matches the name of the attacked company. The ransom note, in addition to contacts for contacting the hackers, also contains a link to a repository with stolen files as evidence of a hack.
Ransom note RA group
The ransomware attacks all logical drives on the victim’s computer and network resources, and tries to encrypt certain folders, excluding those related to the Windows system, downloads, programs, etc. This is done in order not to render the victim’s system inoperable and not to lose the opportunity to receive a ransom.
The RA Group ransomware uses discontinuous encryption (file content is only partially encrypted) to speed up the process. However, this approach allows partial recovery of encrypted data. When encrypting data, the encryptor uses the “curve25519” and “eSTREAM cipher hc-128” algorithms.
Encrypted files are given a “.GAGUP” extension, and all shadow copies and Recycle Bin contents are deleted to prevent data recovery.
The hackers claim to give victims 3 days before posting a sample of the stolen data online. Since this is a new ransomware group with few victims, it is not yet clear how the RA Group’s hackers infiltrate systems and spread over the network.
The RA Group was among the groups that used the Babuk ransomware source code to create their own ransomware even with minimal technical knowledge.
It was previously reported that from September 2021 Several hacker groups took advantage of Babuk ransomware source code leak to create nine different malware families capable of attacking VMware ESXi systems.
Security company SentinelOne said the new variants appeared in the second half of 2022 and the first half of 2023, indicating an increase in the number of hackers using the Babuk source code. Leaking source code allows attackers to attack Linux systems even when they don’t have enough experience to create their own program.
[ad_2]
Source link
www.securitylab.ru