[ad_1]
Microsoft Teams hack: New US Navy tool breaches service security
The red team tool bypasses Microsoft protections and collects data from users of the service.
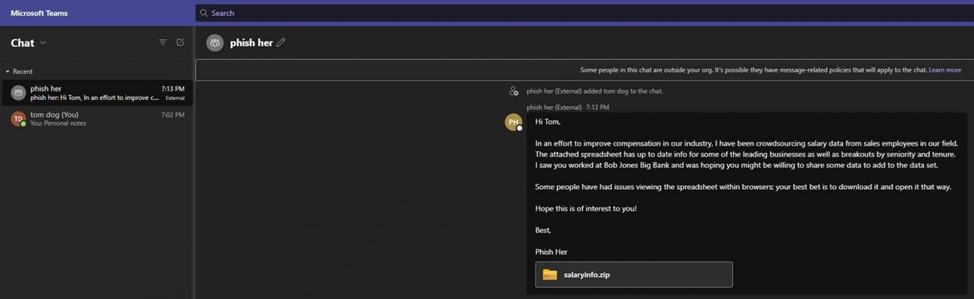
Member of the red teamred team) The US Navy published a tool called Team Phisher which allows you to carry out a phishing attack on users Microsoft Teams. The tool uses an unresolved service security issue to bypass the ban on communication with external users outside the target organization.
The bug allows an attacker to easily bypass Microsoft Teams restrictions on uploading files to deliver malware from an external account. This possibility was discovered by the team jumpsec Labs and described in the technical report firms.
The attack is possible because the Microsoft Teams app has client-side protections that can be tricked into talking to an external user as if it were an internal user by simply changing the ID in the message POST request.
Phishing message through the eyes of the recipient
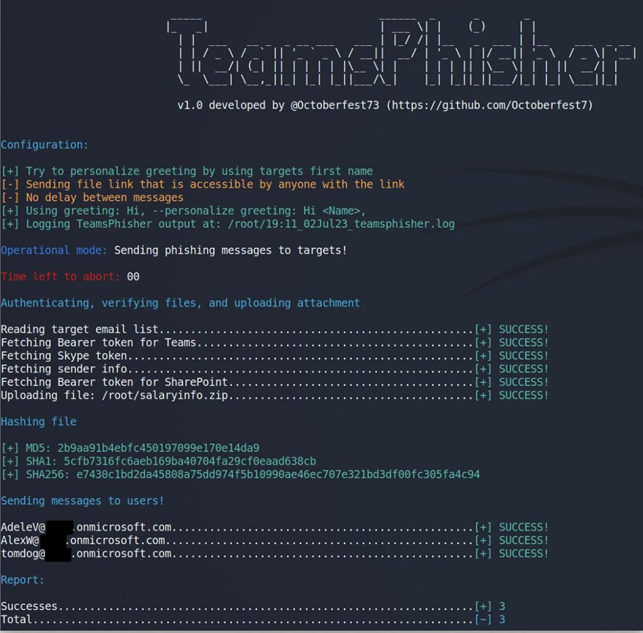
TeamsPhisher first checks for the existence of the target user and their ability to receive external messages, which is a prerequisite for the attack to work.
The tool then creates a new thread with targets, sends them a message with a link to the attachment SharePoint. This displays the thread in the sender’s Teams interface for manual interaction.
Interface Team Phisher
TeamsPhisher requires users to have a Microsoft Business account with a valid Teams and Sharepoint license, which is common with many large companies.
The tool also offers a “preview mode” so that the user can check the target lists and the appearance of the messages for the recipient. TeamsPhisher has other features as well, including:
- sending secure links to files that only a specific recipient can view;
- setting a delay between sending messages to bypass the limit on the frequency of messages;
- writing output to a log file.
The issue that TeamsPhisher is using still exists, and Microsoft has told Jumpsec researchers that it is not a priority for an immediate fix.
Although TeamPhisher was created for the red team, cybercriminals can also use the tool to deliver malware to targeted organizations, bypassing Microsoft Teams security tools.
Until Microsoft takes action on this issue, organizations are strongly advised to disable communications with external users unless they are necessary. Companies can also create a list of trusted domains, which will reduce the risk of exploitation.
[ad_2]
Source link
www.securitylab.ru