[ad_1]
South Korean researchers have invented a hidden CASPER exfiltration method that uses a conventional computer speaker
A tiny detail inside a computer can “blame” all the secret information to hackers.
Researchers at the School of Cybersecurity at Korea University in Seoul have unveiled a new attack called “CASPER”. It takes place over a covert channel and can transmit data from computers without any external connections at a speed of up to 20 bps. Such attacks overcome the so-called “air gap” (“Air Gap”) and are used by cybercriminals where there is no possibility of a direct connection to the target computer either physically or through network protocols.
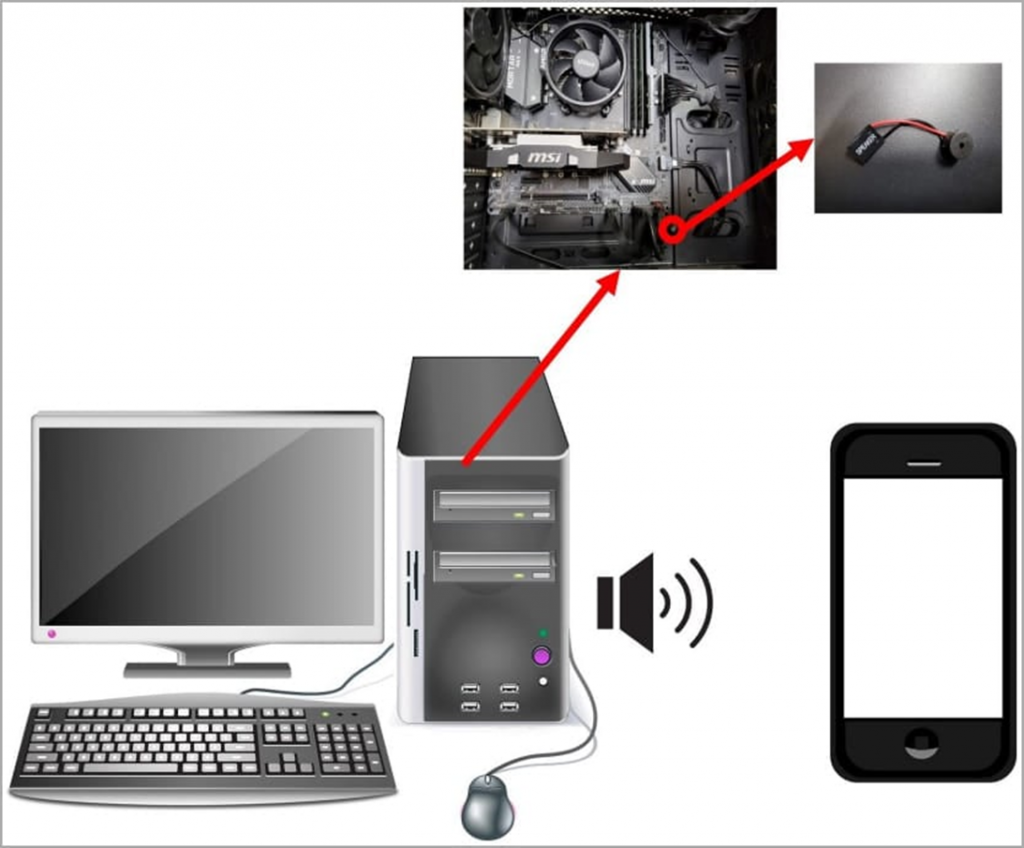
The CASPER attack uses an internal computer speaker connected to the motherboard as a data link. Thanks to special software, the speaker can generate high-frequency sound that is inaudible to the human ear. The sound can be encoded in binary code or Morse code and transmitted to an external receiving microphone. The maximum supported signal transmission distance is 1.5 m, and the microphone itself can be located both in a smartphone and in an intruder’s laptop.
Researchers have previously developed similar attacks using external computer speakers. However, systems isolated from the network used in critical infrastructures are unlikely to be equipped with external speakers. When as internal speakers that beep when the computer starts or in the event of a hardware malfunction, you can still find many computers even in such enterprises.
As with virtually all air gap attacks that target computers isolated from the network, a stealthy attacker with physical access to the target computer must first infect it with malware. For example, through a regular USB flash drive. This process usually takes only a few seconds. But then such a mini-spy “sitting in the computer” can transfer a lot of useful information to the criminal.
While this attack scenario may seem impractical or even far-fetched, there have been several high-profile attacks in the past. A notable example is the Stuxnet worm that targets the Iranian uranium enrichment plant at Natanz. As well as the Agent.BTZ. malware that infected the US military base. This also includes the Remsec modular backdoor, which has been secretly collecting information from closed government networks in different European countries for more than five years.
The malware can autonomously explore the target’s file system, find specific files or file types that match the attacker’s needs, and transfer them to the receiving device. Although with such a low data rate (up to 20 bps), it is more realistic that the speaker will be used as a keylogger, broadcasting the keys pressed on the computer to steal secret passwords.
The program used in the CASPER attack encodes data to be secretly extracted from a compromised device into binary code or Morse code. And then transmits them through the internal speaker of the computer using frequency modulation. As a result, the data is transmitted in the form of ultrasound, which is imperceptible to the human ear, in the frequency range from 17 kHz to 20 kHz.
The researchers used a Linux computer Ubuntu 20.04 as the target and a Samsung Galaxy Z Flip 3 as the receiver in their experiment. Scientists have experimented a lot with the frequency, duration of the signal and the distance from which this signal can be received without interference. Based on the tests carried out, the maximum distance to the receiver was 1.5 meters. However, for the most stable and fastest data transfer, the distance should be even shorter.
At this data rate, malware can transfer a standard 8-character password in about 3 seconds, and a 2048-bit RSA key in as little as 100 seconds. At the same time, it will take more than an hour to transfer a typical Microsoft Word document of, say, 10 KB, even if conditions are ideal and there are no interruptions during the transfer.
“Our method transmits data more slowly compared to other covert channel technologies using optical or electromagnetic methods, because the data transfer rate over sound is physically limited,” the South Korean researchers said.
The solution to the problem of low data rates, according to the scientists, would be to change the frequency band for multiple simultaneous transmissions, but internal computer speakers can only reproduce sound in one frequency band.
The researchers also shared ways to defend against a CASPER attack. The simplest of them was the banal extraction of the internal speaker from critical computers. However, if this is not possible, security professionals can embed a high-pass filter into the computer to keep all generated frequencies within the audible audio spectrum, blocking the transmission of ultrasound. Thus, potential victims will at least hear how the attacker is slowly but surely stealing their data.
We have previously written about other types of covert channel attacks using the air gap technique. For example, COVID bit developed last year, used a computer power supply to generate electromagnetic waves that receiving equipment could pick up at a distance of two meters.
[ad_2]
Source link
www.securitylab.ru