[ad_1]
NATO horrified: Winter Vivern steals government letters through Zimbra vulnerability
The researchers are sure that only the negligence of foreign “security guards” allowed hackers to take advantage of a security hole.
The alleged Russian cybercriminal group, tracked under the code name TA473 or “Winter Vivern” (“Winter Wyvern”), has been actively exploiting vulnerabilities in unpatched Zimbra endpoints since February 2023 to steal emails from NATO officials, governments, military personnel and diplomats.
Two weeks ago SentinelLabs informed O recent operation Winter Vivern using sites imitating European cybercrime agencies to distribute malware.
Today the company Proofpoint published a new report on how attackers exploit CVE-2022-27926 on the Zimbra Collaboration servers to access messages from organizations and individuals associated with NATO.
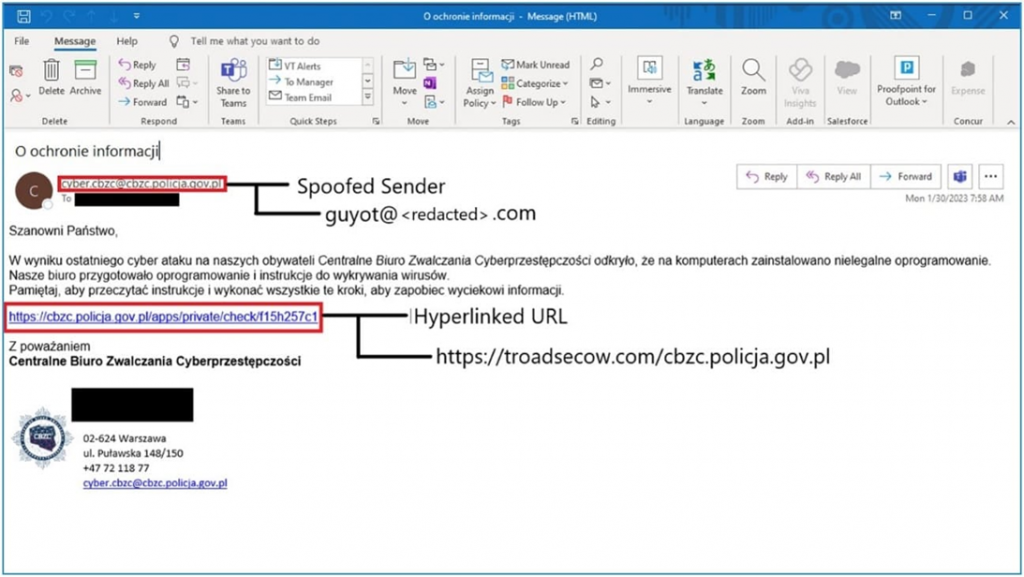
Winter Vivern attacks begin with cybercriminals looking for unpatched (not updated to the latest version) Zimbra endpoints using the Acunetix vulnerability scanner. The hackers then send a phishing email from the hacked address. This letter is forged in such a way that the victim is sure that the sender is her friend or colleague.
Email from Winter Vivern
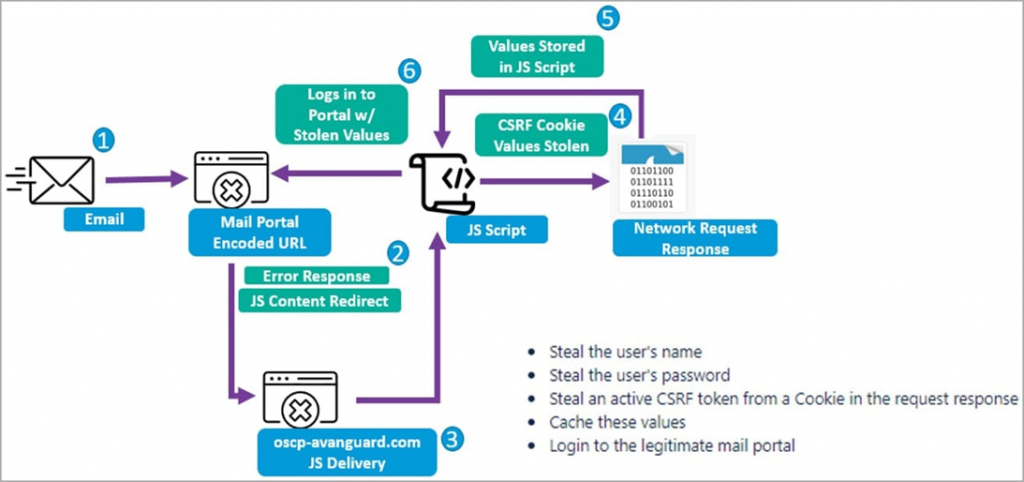
The emails contain a link that uses CVE-2022-27926 in a compromised Zimbra infrastructure to inject malicious scripts JavaScript to a web page. These scripts are then used to steal usernames, passwords, and tokens from cookies received from the compromised Zimbra endpoint. This information allows attackers to freely access the email accounts of the targets. “These blocks of JavaScript CSRF code are executed by the server hosting the vulnerable webmail instance,” Proofpoint explains in their report.
Complete chain of attacks
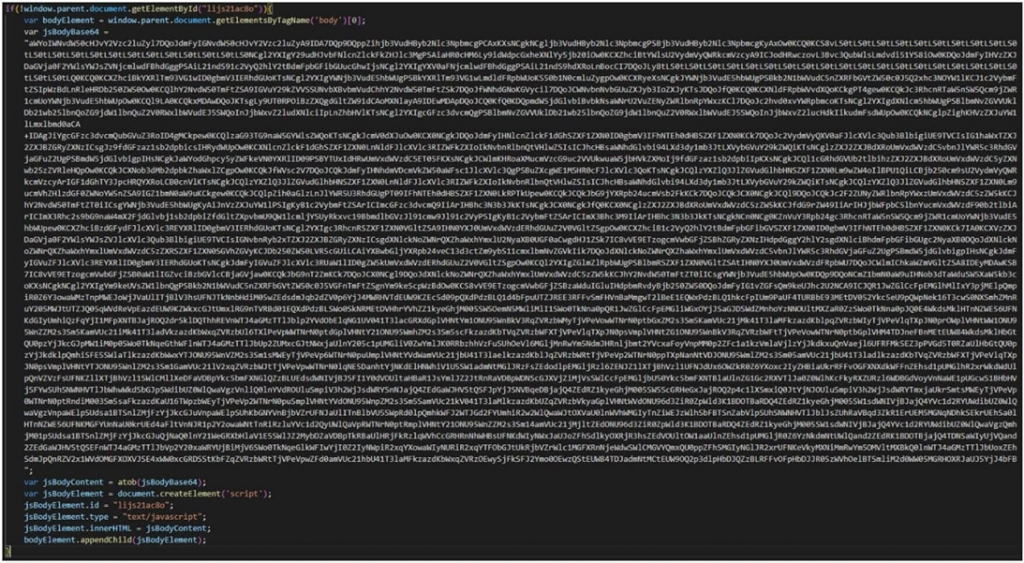
In addition to the three levels of obfuscation base64applied to malicious JavaScript code for more complex analysis, Winter Vivern also leaves parts of legitimate JavaScript code mixed in with normal operations and reduces the chance of detection.
Obfuscated JavaScript
Finally, attackers can gain access to sensitive information on compromised email websites or retain control over messages for a period of time. In addition, hackers can use hacked accounts to carry out side phishing attacks and further infiltrate targeted organizations.
Although the researchers state that the Winter Wyvern does not use particularly sophisticated methods, they maintain an efficient operational approach that works even against high-profile targets. The latest malware campaigns of this group clearly show why you should not delay software updates. After all, hackers exploited a vulnerability that was fixed in Zimbra Collaboration version 9.0.0 P24, released 10 months ago, in April 2022.
[ad_2]
Source link
www.securitylab.ru