[ad_1]
Sharp Panda Hackers Use Radio Silence Malware
An unusual feature allows the program to go unnoticed on a compromised device for a long time.
Cyber-espionage hacker group Sharp Panda is targeting high-ranking government agencies in Vietnam, Thailand and Indonesia with a new version of malware called Soul.
Specialists checkpoint revealed new campaign using this software. It started at the end of 2022 and is still ongoing. Attackers use spear-phishing attacks to initially compromise.
CheckPoint was able to attribute the latest spying operation to state-backed Chinese hackers in a number of ways. Tactics, methods and tools used correspond to the previously seen activities of the Sharp Panda faction.
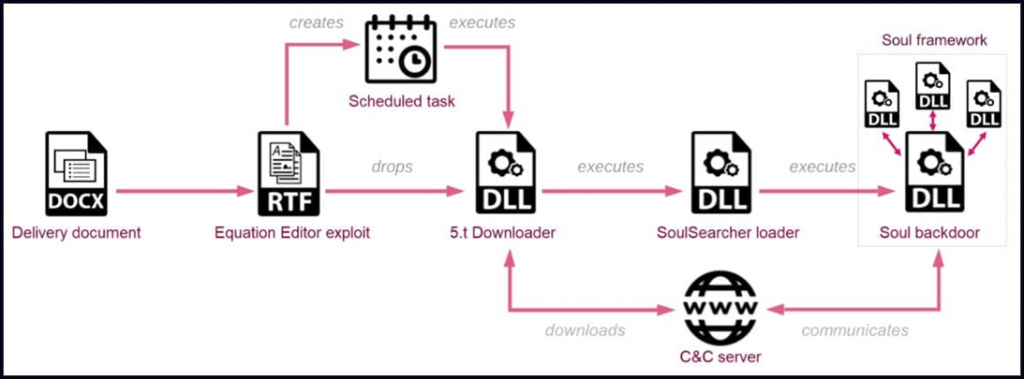
In its new malware campaign, Sharp Panda uses phishing emails with malicious attachments in the form of “.docx” files. They are needed to deploy the RoyalRoad suite and compromise the system through known vulnerabilities. The exploit creates a scheduled task and then downloads and runs the malware downloader. DLLwhich in turn loads the SoulSearcher loader itself.
Soul malware in the latest Sharp Panda campaign
When launched, the main module of the Soul malware establishes a connection with the C2 server and waits for the download of additional modules that extend its functionality.
The new version of Soul, analyzed by CheckPoint, has an interesting “radio silence” mode that allows attackers to specify certain days of the week and time of day when backdoor must not contact the C2 server to avoid detection.
In addition, the new version implements its own protocol for communicating with the C2 server, which uses various HTTP request methods, including GET, POST, and DELETE. This feature gives the backdoor considerable flexibility in application.
Soul’s connection with the C2 server begins with registering on the network and sending the victim’s data (hardware information, OS type, time zone, IP address, etc.), after which the malware enters an endless loop of communication with the server. Commands it may receive during this communication include loading additional modules, collecting and resending data, restarting the connection, or dropping the connection entirely.
The Soul framework was first seen in 2017 and subsequently tracked throughout 2019 in Chinese spying campaigns run by attackers with no apparent ties to Sharp Panda. Despite the solid age of Soul, CheckPoint experts concluded that the malware is still at the development stage, its functionality and ways of evading detection will only be supplemented in the future.
[ad_2]
Source link
www.securitylab.ru